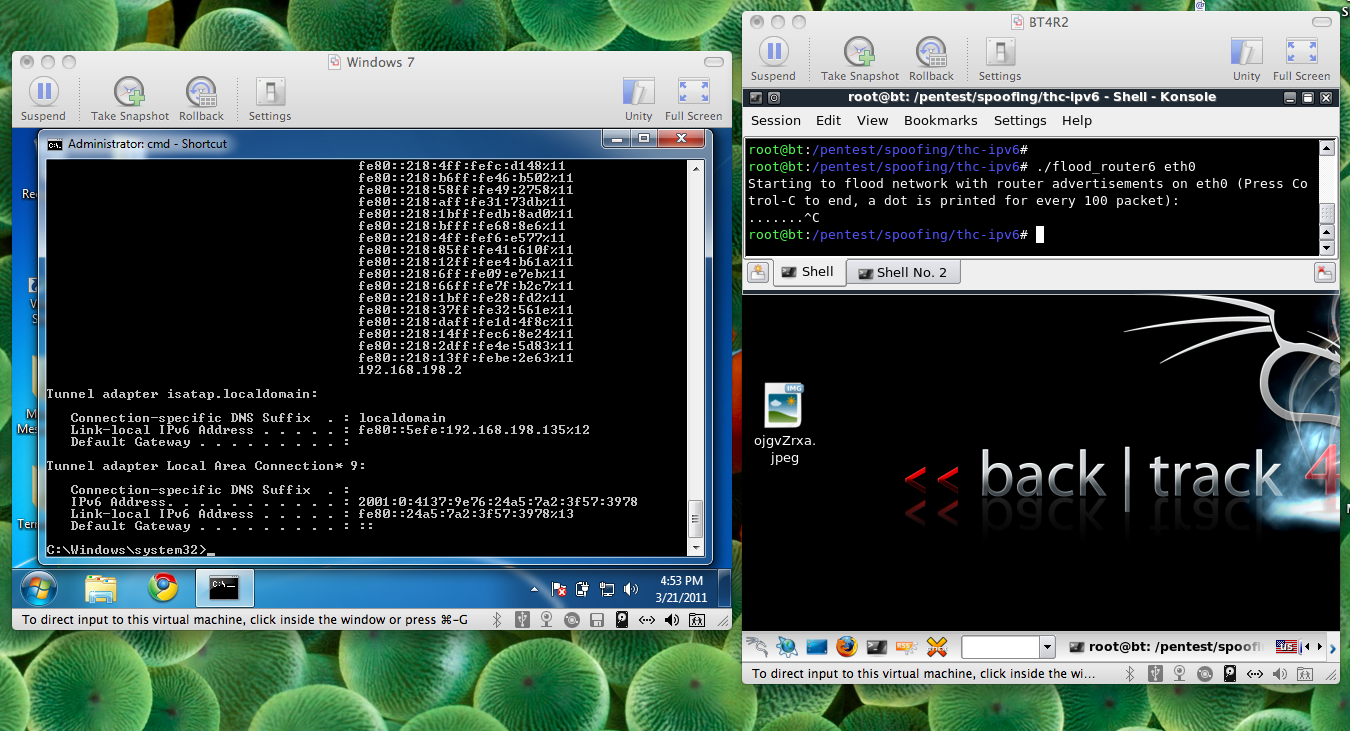
This will not be a good homework assignment, I decided, because students will just crash the machines before they can examine them. But wait--Router Advertisements are not unicast traffic! They are sent to ff02::1, the "all-nodes multicast address", so this single Linux machine will stop every Windows machine on a whole network. And all the Windows servers too!
This was too hot to handle, so I sent out some frantic tweets, asking for a security contact inside Microsoft, ASAP. And my friends came through--within a few hours I had reached the right people, and within two days I had Microsoft's response. Here's what they said:
1. This was not news to them. As I later found out, Microsoft had been alerted to this in July of 2010.
2. They don't care. Microsoft has no intention of patching this at all.
Whoever made those decisions at Microsoft has simply not thought it through. What will they say when a whole financial company goes down, or a government office, or industrial machinery, or a hospital, because of this attack? How can they escape liability when it is a matter of public record that a serious defect exists in their products and they do nothing?
This is a common situation in the field of network security: you find something AWFUL, and management ignores you. I often discuss this with my students. Common responses are to get drunk, start insulting your bosses, sabotage your own network, send secrets to Wikileaks, etc. Those are the self-destructive, counterrproductive responses which I don't recommend. The right thing to do is inform and protect people in a reasonable manner.
So here's what I did. I wrote a weaker, slower form of the attack so it could be used as homework without crashing the target machine, and also ported it to Windows, so I can easily use it in classes and demonstrations. And I wrote a talk proposal for Black Hat, the most important security conference in the world for CSO-level executives. If my talk is accepted, I will go there and kill a network of Windows machines on stage. And I will tell them how to protect their machines. So they will be safer, and perhaps they will go suggest to Microsoft that they think again about just leaving this hole unplugged.
If you want more information, and several projects ready to use in classes, see this page:
http://samsclass.info/ipv6/proj/flood-router6a.htm. I have also listed ways to protect yourself there.

Nice work, Sam!
ReplyDelete